We can control access to SharePoint Online and OneDrive resources based on defined network locations that you trust. This is also known as location-based policy.
OneDrive is basically a SharePoint MySite. Though they have separate admin center, both are inter linked.
Note: Microsoft recommends that when a location-based policy is enabled for SharePoint, the same policy and IP address ranges should be configured for Exchange and Yammer. SharePoint relies on these services to enforce that the users of these apps are within the trusted IP range.
First, get the authorized IP address ranges of your trusted network boundary. We need to set them in SharePoint admin center or OneDrive admin center. [If you do in SharePoint admin center, it will automatically reflect in OneDrive admin center].
SP admin center
OD admin center
Any user who attempts to access SharePoint and OneDrive from outside this network boundary (using web browser, desktop app, or mobile app on any device) will be blocked and will get Access restricted message in browser.
Set a location-based policy using Windows PowerShell
2. Connect to SharePoint Online as a global admin or SharePoint admin in Office 365. To learn how, see Getting started with SharePoint Online Management Shell.
3. Run Set-SPOTenant to specify your allowed IP addresses, as in this example (replace the example IP address "131.102.0.0/16" with your own):
Set-SPOTenant -IPAddressAllowList "131.102.0.0/16"
Important Note:
- Use IPv4 or IPv6 formats ony.
- Verify that there are no overlapping IP address ranges.
- Double check the IP range(s) before enabling this policy to ensure you do not lock yourself out.
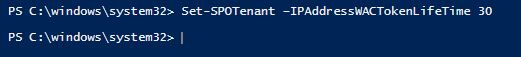
4. Enforce the allowable IP ranges you just set as in this example:
Here are some important considerations for setting a location-based policy:
External Sharing: As per the policy, users who try to access SharePoint resources from outside the defined IP address range will be blocked, including guest users outside of the range with whom files have been externally shared.
Access from first and third-party apps: Normally, a SharePoint document can be accessed from apps like Exchange, Yammer, Skype, Teams, Planner, Flow, PowerBI, PowerApps, OneNote, and so on. When a location-based policy is enabled, apps that do not support location-based policies are blocked. The only apps that currently support location-based policies are Yammer and Exchange. This means that all other apps are blocked, even when these apps are hosted within the trusted network boundary. This is because SharePoint cannot determine whether a user of these apps is within the trusted boundary.
For Example: You cannot add OneNote in the Microsoft Teams. When you try to add OneNote in Microsoft Teams, it shows you permission error even though you were owner for that Team.
Access from dynamic IP ranges: Several services and providers host apps which have dynamic originating IP addresses. For example, a service that accesses SharePoint while running from one Azure data center may start running from a different data center due to a failover condition or other reason, thus dynamically changing its IP address. The location-based conditional access policy relies on fixed, trusted IP address ranges. If the IP address range cannot be determined up front, location-based policy may not be an option for your environment.